Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
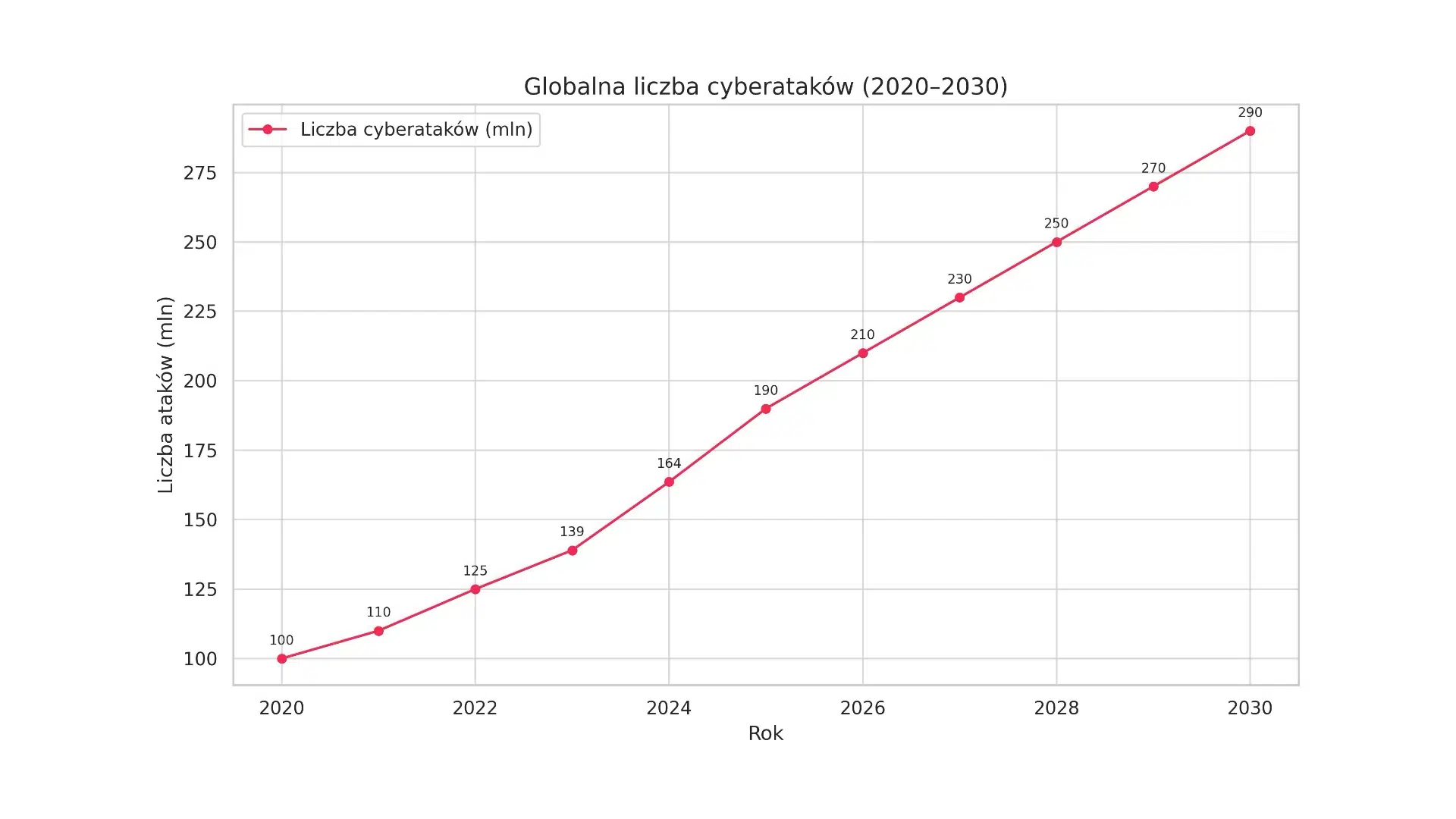
Today’s digital landscape presents business leaders with a paradox: despite increasing investment in cyber security, the number and scale of incidents are not decreasing – quite the opposite. This is causing concern among executives and undermining the effectiveness of existing strategies. Cyber security, once the domain of IT, has now become a key management topic. The Allianz Risk Barometer 2024 report confirms this, identifying cyber incidents as the biggest global business risk.
The scale of the threat is enormous. By 2025, losses from cybercrime are expected to reach $10.5 trillion annually. The average cost of a data breach in 2024 rises to $4.88 million – up 10% year-on-year, reaching an all-time high. At the same time, spending on information security is expected to reach $212bn in 2025, up 15.1% from 2024 ($183.9bn – Gartner data).
This parallel increase in expenditure and incidents is the so-called 'cyber arms race’. Organisations are increasing budgets to keep up with increasingly sophisticated attacks, often based on AI. Investment does not eliminate threats, but only reduces their impact – the goal becomes resilience, not total security.
The increase in the cost of breaches despite higher expenditure suggests that the allocation of resources may be suboptimal. The effectiveness of investments is still sometimes difficult to prove and the expected return is lower than expected.
Despite increasing spending, business and cyber security leaders are grappling with an increasingly complex and dynamic threat landscape.
Evolution and scale of incidents
One in three CEOs see cyber espionage and loss of intellectual property as the biggest threats, while 45% of cyber security leaders are concerned about operational disruption. Image damage and loss of customer trust are also among the key worries. The increasing complexity of threats – driven by technological advances, supply chain integration and geopolitical tensions – exacerbates the risks. In addition, up to 76% of CISOs indicate that fragmented regulations across jurisdictions make it difficult to ensure regulatory compliance.
A new dimension of threats: GenAI
Generative AI not only creates new risks, but changes the nature of known ones – especially in the area of social engineering. With its ability to mimic communication styles, phishing becomes harder to detect and the human element a prime target for attacks. As a result, defence strategies must focus not only on technology, but also on employee education and awareness-raising.
Growing investment in cyber security: where does the money go?
In the face of growing threats, companies are significantly increasing cyber security budgets, treating it as a strategic element of risk management.
Global expenditure
Global spending on information security is expected to reach $212bn in 2025, up 15.1% from 2024 ($183.9bn – Gartner forecasts). IDC forecasts a 12.2% year-on-year increase. In turn, 63% of companies plan to increase their cyber security budgets, including training (HCLTech Cyber Resilience Study 2025).
Investment priorities:
The increase in spending on AI and automation is a reaction to increasingly sophisticated AI-assisted attacks. A 'cyber arms race’ is emerging in which both sides – attackers and defenders – are constantly upgrading their technology. The effectiveness of these investments depends on the thoughtful integration of AI rather than a haphazard proliferation of tools.
The growing investment in Zero Trust Architecture (ZTA) reflects a shift in approach: from a perimeter to a model of continuous verification and minimum privilege. In the age of remote working and distributed infrastructure, traditional network protection is losing its effectiveness. ZTA assumes that no one – inside or outside – is trusted by default. High adoption and market growth show that this is not a temporary trend, but a necessary evolution of security strategy.
This paradox is due to a number of interrelated factors that undermine the effectiveness of classic defence strategies.
Complex IT environments and point solutions
Medium and large companies use 51-58 different security tools, leading to overloaded IT teams and inattention to vulnerabilities. According to Cisco, up to 80% of companies believe that an excess of 'point solutions’ hinders detection, response and recovery from incidents.
The growing number of IoT devices – often with default passwords and poor support – creates billions of entry points. Additionally, the integration of legacy systems with modern infrastructure and the rapid adoption of the cloud are increasing the complexity and vulnerability of hybrid environments.
The paradox of AI: implementation without safeguards
Although 66% of companies believe AI will have the biggest impact on cyber security in the coming year, only 37% assess the security of AI tools before deployment. As many as 53% of organisations do not have adequate safeguards against AI-based attacks (VikingCloud 2025), revealing a serious gap between risk awareness and deployment practice.
The competence gap in cyber security
The skills gap has increased by 8% since 2024, with two-thirds of organisations reporting moderate to severe staff shortages. Only 14% of companies believe they have the right team. Globally, there is a shortage of 4 million cyber security professionals, increasing the cost of breaches by an average of US$1.76 million. The SME and public sectors are particularly affected, with staff shortages leading to overstretched and burned-out teams.
Risks in supply chains
93% of companies have experienced breaches through vulnerabilities at suppliers, and 29% of all incidents originated from external partners. Lack of oversight and transparency in supply chains is one of the main risks in cyber security today.
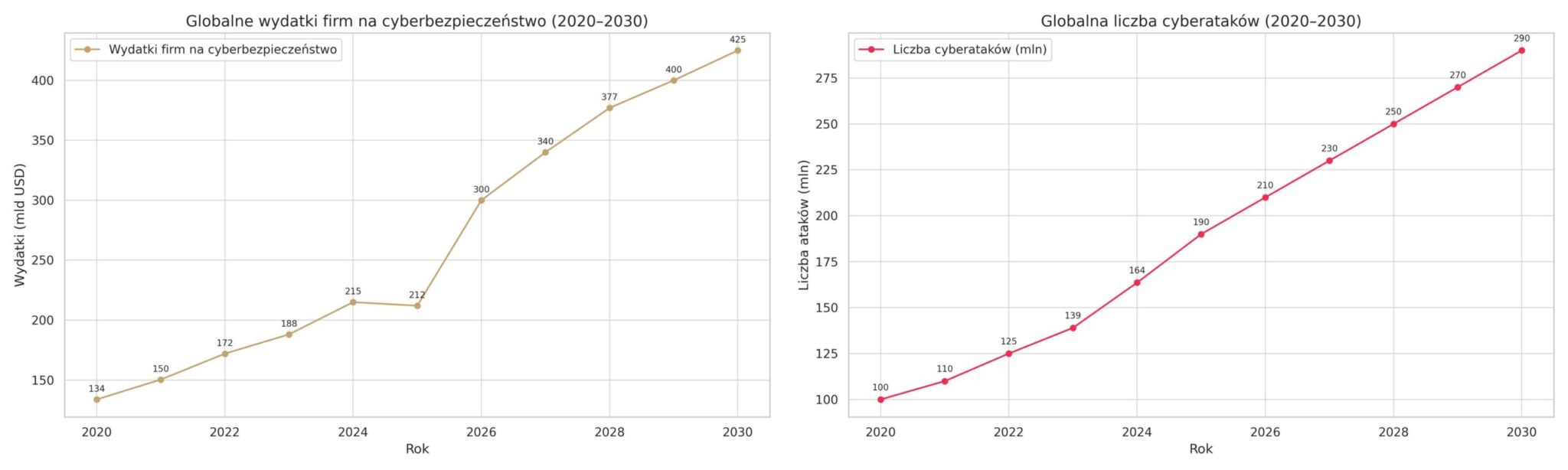
Overcoming the paradox of increasing incidents despite greater investment requires a shift from response to integrated, proactive resilience – taking into account both technology and the human factor.
Zero Trust as the new standard
Zero Trust, based on the principle 'never trust, always verify’, is becoming the new norm. Gartner predicts that by 2025. 60% of companies will adopt ZTA as the foundation of security and by 2026, 81% will have implemented it. ZTA can reduce the cost of data breaches by US$1m and addresses the challenges of cloud, supply chain and human risk.
Consolidation of tools – fewer but more effective
Current, distributed systems cannot cope with modern threats. By 2028. 45% of companies will reduce the number of tools in use to fewer than 15 (vs. 13% in 2023). Unified platforms increase efficiency, visibility and enable AI analytics, reducing detection and response times to minutes.
AI as a pillar of SOC – responsibly and purposefully
AI supports threat detection and automates responses. Implementing 'tactical AI’ – focused on measurable outcomes and consistent with KPIs – is key. Building trust requires transparency in models, data sources and decisions.
Secure supply chains
By 2025. 60% of organisations will make decisions about working with suppliers based on their risk profile. Partner security assessments and the application of ZTA to third parties will become key.
Investment in people and safety culture
Competence development is a priority. Training, certification and user education – e.g. phishing programmes with a 50x ROI – are essential. Organisations need to foster a culture of shared responsibility for cyber security and develop 'cyber-judgement’ at every level.
Public-private cooperation – the foundation of collective resilience
Stronger cooperation between the public and private sectors and at the international level is key to countering cross-border threats and harmonising security policies.
Cyber-resistance instead of prevention alone
Organisations are shifting their focus from prevention to resilience – the ability to survive, respond and recover quickly from an incident. By 2025, around 70% of CEOs will have introduced resilience as part of their organisational culture.
New technologies – preparing for tomorrow
Companies should already be implementing post-quantum cryptography (PQC) standards to protect themselves against future threats from quantum computers.
The combination of Zero Trust adoption and tool consolidation is a response to 'sprawl’ and complexity, identified as the main sources of defence ineffectiveness. Zero Trust requires continuous verification and precise controls, which is difficult to achieve with distributed systems. Unified platforms centralise data and operations, making ZTA easier to implement. These two trends work synergistically to simplify and strengthen cyber security.
The growing emphasis on measurable return on security investment is transforming the perception of the CISO – from a technical supervisor to a strategic partner. Executives expect real results: shorter downtimes, avoided penalties, improved reputation. CISOs must therefore translate security into the language of the business, fostering a lasting commitment and embedding security into the organisational culture.
The message to CEOs is clear: cyber security is no longer just a cost or IT issue, but a key element of business continuity, innovation and competitive advantage. In an era of rising incident costs and the importance of digital operations, effective protection directly affects finances, reputation and stability. Only a strategic, holistic approach – taking into account the complexity of the environment, people and competencies – will allow companies to safely thrive in an increasingly hostile digital environment. It is a shift in perspective: from 'what we fear’ to 'how we protect our future’.